Crypto Generate Rsa Key
To perform operations like signing and encrypting you pass a CryptoKey object into the sign or encrypt function. I have switch 3548-XL with version 12053WC.
How To Configure Ssh On Cisco Ios
You can use the openssl command to decrypt the key.
. Bits integer Key length or size in bits of the RSA modulusIt must be at least 1024 but 2048 is recommended. Current running confing I cant see crypto pki certificate. Expanding more than I feel is appropriate for an edit PKCS1 available in several versions as rfcs 2313 2437 3447 and 8017 is primarily about using the RSA algorithm for cryptography including encrypting decrypting signing and verifyingBut since crypto is often used between systems or at least programs it is convenient to have a defined interoperable format.
A key object can be created in four ways. A key in cryptography is a piece of information usually a string of numbers or letters that are stored in a file which when processed through a cryptographic algorithm can encode or decode cryptographic data. For ECDSA or ECDH.
SPKAC is a Certificate Signing Request mechanism originally implemented by Netscape and was specified formally as part of HTML5s keygen element. Asymmetric keys are represented by Python objects. Use this command to generate RSA key pairs for your Cisco device such as a router.
The problem with RSA is its source of randomness. Generate an ECDSA SSH keypair with a 521 bit private key. Cipher message to decrypt.
Openssl rsa -pubout -in private_keypem -out public_keypem Extracting the public key from an. The FIPS standard only defines 1024 2048 and 3072. The original specification for encryption and signatures with RSA is PKCS 1 and the terms RSA encryption and RSA signatures by default refer to PKCS 1 version 15.
E integer Public RSA exponentIt must be an odd. Display private rsa key if recovered. You can see this using openssl asn1parse and -strparse 19 as described in this answer.
If your router already has RSA keys when you issue this command you will be warned and prompted to replace the existing keys with new keys. Pass an HmacKeyGenParams object. For AES-CTR AES-CBC AES-GCM or AES-KW.
RSA is a single fundamental operation that is used in this package to implement either public-key encryption or public-key signatures. For RSASSA-PKCS1-v1_5 RSA-PSS or RSA-OAEP. Generating and deriving keys.
Inspecting the output file in this case private_unencryptedpem clearly shows that the key is a RSA private key as it starts with -----BEGIN RSA PRIVATE KEY-----. Pass an RsaHashedKeyGenParams object. The generateKey and deriveKey functions both.
Randfunc callable Function that returns random bytesThe default is CryptoRandomget_random_bytes. Generate a random private key and public key the size is 1024-4096 bits. Ssh-keygen -t ecdsa -b 521 -C ECDSA 521 bit Keys Generate an ed25519 SSH keypair- this is a new algorithm added in OpenSSH.
Based on the used method the key can be different sizes and varieties but in all cases the strength of the encryption relies on the security of the key being maintained. Each object can be either a private key or a public key the method has_private can be used to distinguish them. This non-elliptic crypto algorithm which is based on prime numbers generates a relatively insecure key pair when you pick a key size below 2048-bits.
The second half of the course discusses public-key techniques that let two parties generate a shared secret key. Openssl rsa -in pathtoencryptedkey -out pahttodecryptedkey For example if you have a encrypted key file sslkey and you want to decrypt it and store it as mykeykey the command will be. The most common usage is handling output.
There are many libraries available in python for the encryption and decryption of a message but today we will discuss an amazing library called pycryptodome. RSA Encryption Implementation Using Library in Python. RSA in particular and the other.
Ssh-keygen -t ed25519 Extracting the public key from an RSA keypair. Public rsa key to crack. CryptoPublicKeyRSAgenerateThe key is randomly created each time.
That changes the meaning of the command from that of exporting the public key to exporting the private key outside of its encrypted wrapper. I have 841 router after factory reset i unable to find crypto pki certificate chain TP-self-signed How can I generate crypto pki certificate please guide. Generate at the module level eg.
Thanks for using this software for CofeeBeerAmazon bill and further development of this project please Share. Is deprecated since HTML 52 and new projects should not use this element anymore. In a second course Crypto II we will cover more advanced cryptographic tasks such as zero-knowledge privacy mechanisms and other forms of encryption.
Perform the signature verification operation defined in Section 81 of with the key represented by the internal slot of key as the signers RSA public key and the contents of message as M and the contents of signature as S and using the hash function specified by the hash attribute of the internal slot of key as the Hash option MGF1. SSH Config and crypto key generate RSA command. Except for digest all the cryptography functions in the API use cryptographic keysIn the SubtleCrypto API a cryptographic key is represented using a CryptoKey object.
DSA key pairs should not be used anymore. The key-label argument must match the key pair name that was specified through the crypto key generate rsa command. You can import multiple public keys with wildcards.
RSA is not vulnerable but the source of entropy is the weakest link in the RSA algorithm. Any private key value that you enter or we generate is not stored on this site this tool is provided via an HTTPS URL to ensure that private keys cannot be stolen for extra security run this software on your network no cloud dependency. The RSA algorithm provides.
Pass an EcKeyGenParams object. Attack RSA specify --publickey or n and e publickey. An object defining the type of key to generate and providing extra algorithm-specific parameters.
What you get in an RSA PUBLIC KEY is closer to the content of a PUBLIC KEY but you need to offset the start of your ASN1 structure to reflect the fact that PUBLIC KEY also has an indicator saying which type of key it is see RFC 3447. IP200conf t Enter configuration commands one per line. RSA key pair will be displayed in PEM format on the console terminal.
URL of the file system. Create a Public Key File Given n and e specify --createpub n. As per your above comment TP-self-signed-4147111382 how can i Find this number for my router.
Visually Inspect Your Key Files. The nodecrypto module provides the Certificate class for working with SPKAC data. When attempting to run crypto key genearte rsa it doesnt work.
Keys are generated in pairsone public RSA key and one private RSA key.
Crypto Key Generate Rsa General Keys Label Turbogalaxy
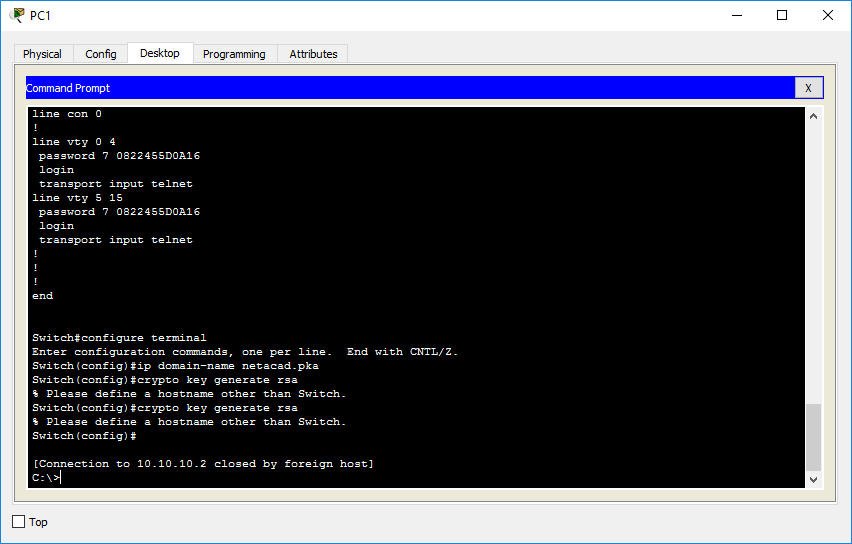
Crypto Key Generate Rsa Please Define A Hostname Other Than Switch Cisco Community

No comments for "Crypto Generate Rsa Key"
Post a Comment